Context:
- Difficulty: Easy
- Author: stuxnet
- Link: https://tryhackme.com/room/bsidesgtdav
Overview:
A machine tailored towards beginners, Dav focuses on exploiting WebDav, which expands the standard of HTTP headers and methods and allows a user to create, move and edit files, as well as, being able to delete or copy them. As a result, the web server almost functions like a file server. Note: Sometimes authentication is required to access the /webdav folder.
Learning moments: Dav will provide a better understanding of what can occur when default credentials are not changed, and furthermore, provide evidence of exploitable sudo access to a non-privileged user.
Reconnaissance:
- Nmap: As always, a thorough nmap scan of the machine was conducted and the contents saved to a file named scan. All 65535 ports were scanned, and aggressive detection was enabled. The timing was set to 4 (higher is faster). Output:
- Gobuster: HTTP is running; thus we can perform a directory brute-force of possible folders which may direct our exploitation. Command: gobuster dir -w /opt/dir/directory-list-2.3-medium.txt -u 10.10.231.115
Output: A /webdav folder was found; corresponding with the name of the machine. Let's take a look at the server. **Note:** the IP address changed as the machine restarted.

The server is asking for credentials. While a brute-force is possible, finding default credentials may be a viable first option, before taking those steps. It may save time. A quick search for webdav default credentials leads to this site.
Exploitation:
Inputting those default credentials provides us with direct access. A file passwd.dav is located within this directory. It contains the hash of the default user's password.
Output:

Hash:

- Cadaver: The techniques available for exploiting WebDav are listed here. The simplest? Install cadaver which is a command-line client for Unix-based systems and upload a reverse shell onto the /webdav folder.
Output:
- Netcat: The reverse shell has been uploaded to the folder. Now, we must open a listening connection, and wait for the machine to connect to our attacking machine. Command:
nc -nvlp 4444Heading over to the web-server, simply clicking the reverse shell will initiate a connection.
Output:

Over on the attacking machine, there is a successful remote connection.

Privilege escalation
Knowing the level of access the current user has is vital. The command: sudo -l lists a user's sudo privileges. Sometimes, this command may ask you for a password; if it is not known, then unfortunately, this will not work.
Output:

The (ALL) NOPASSWD: /bin/cat line informs the user that this binary can be run with sudo privileges. As a result, we can output the contents of any file. Files usually secured by safe permissions like /etc/shadow are now vulnerable to being openly readable by a low-privilege user. Thus, user password hashes can then be copied and cracked offline.
Output:

The command works. This means we can print out the contents of any file that we wish. There are two we are particularly interested in: user.txt and root.txt. Firstly, however, we must find exactly where these files are located. The find command will be most useful here.
Commands:
-
find / -name user.txt 2>/dev/null -
find / -name root.txt 2>/dev/null
The / tells find to search in the root directory for a specific name. In this case, user.txt and root.txt. The 2>/dev/null ensures that errors are not visible in the output. However, the find command will produce no output (in my case) when finding root.txt. Although, fortunately, it usually resides in /root/root.txt.
Output:

We can now print the contents of these files.

Conclusion
The machine has been successfully exploited. This machine provides us with a few learning moments. In order to eradicate these flaws, one should:
-
Firstly, change default user credentials and remove the hash file from such an an easily accessible folder.
-
Secondly, change the level of privilege
www-datahas. This line within/etc/sudoersmust be removed immediately.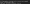
If this was a real machine, the company would strongly be recommended the principle of least-privilege. Here, users are given the minimum levels of access or permissions needed to perform a particular job or function. A web server user should not have this type of access.











